Countless Asus routers have been compromised and are currently controlled by a group believed to be linked to the Chinese government, which has not disclosed its plans for the widespread breach, researchers reported.
The hacking campaign appears to focus on seven specific models of Asus routers, all of which have reached end-of-life status with the manufacturer, indicating they no longer receive updates for security vulnerabilities, according to researchers from SecurityScorecard stated. At this stage, it remains uncertain what actions the perpetrators take once they seize control of the devices. SecurityScorecard has designated this operation as WrtHug.
Avoiding detection
SecurityScorecard suggested that the hacked devices might be utilized in a manner akin to that of ORB (operational relay box) networks, which are adopted by hackers mainly for espionage purposes to obscure their identities.
“Possessing this degree of access could allow the threat actor to employ any compromised router according to their preference,” noted SecurityScorecard. “Our knowledge of ORB networks indicates that compromised devices are typically used for clandestine actions and espionage, rather than DDoS attacks and other forms of overt malicious conduct generally seen from botnets.”
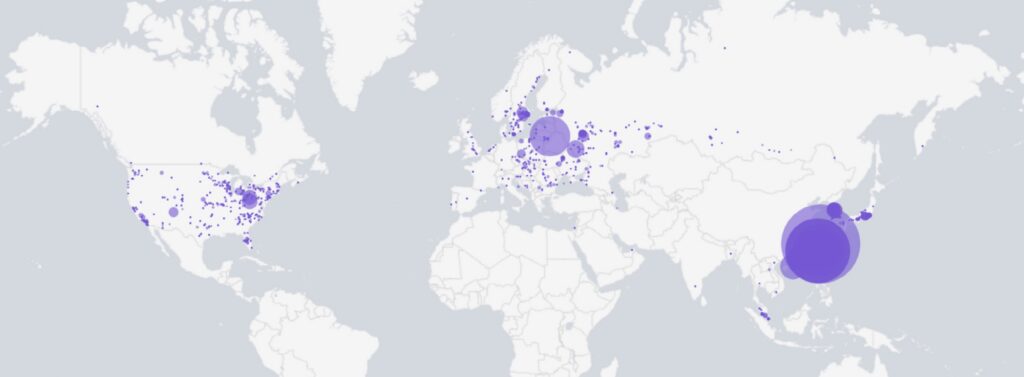
Infected routers are predominantly found in Taiwan, with smaller groups present in South Korea, Japan, Hong Kong, Russia, central Europe, and the United States.
A heat map showing infected devices.
The Chinese government has been recognized for constructing extensive ORB networks for several years. In 2021, the French government alerted national enterprises and organizations that APT31—one of China’s most active threat entities—was responsible for a significant attack campaign using hacked routers for reconnaissance. Last year, at least three comparable Chinese-led operations were uncovered.
Russian state-sponsored hackers have been discovered engaging in similar activities, albeit less frequently. In 2018, Kremlin-affiliated actors compromised over 500,000 small business and home routers with advanced malware identified as VPNFilter. A group linked to the Russian government was also involved in an operation highlighted in one of the 2024 router breaches mentioned earlier.