Establishing or adjusting smart contracts generally incurs costs below $2 for each transaction, representing a significant reduction in both financial resources and labor compared to more conventional approaches for disseminating malware.
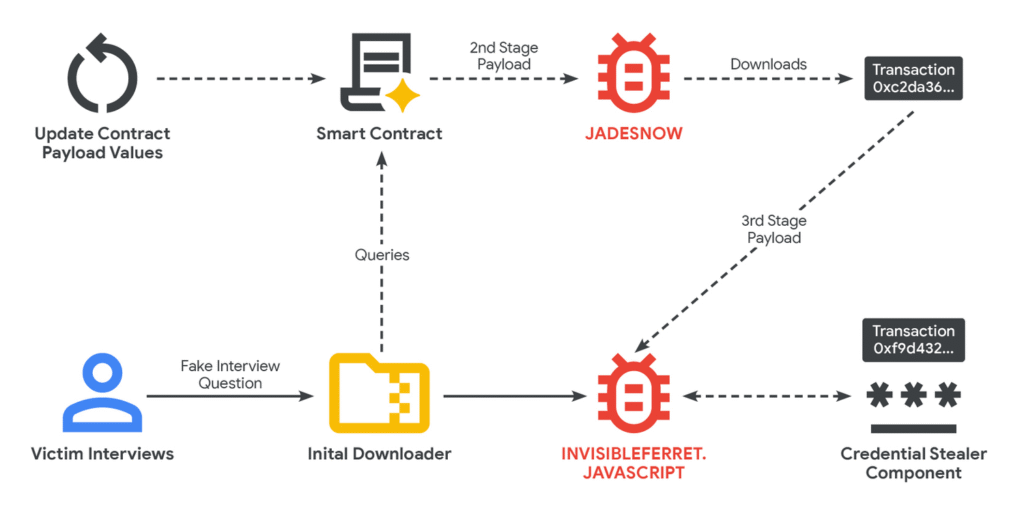
On top of the EtherHiding strategy that Google identified, there was a social-engineering initiative that employed fake job recruiting to entice targets, a large number of whom were developers of cryptocurrency applications or other online services. Throughout the vetting phase, applicants are required to undergo a test showcasing their coding or code-review abilities. The documents necessary for completing the tests contain hidden malicious code.
Depiction of the UNC5342 EtherHiding procedure.
The infection sequence depends on a series of malware that is progressively installed in stages. Subsequent stages that are responsible for executing the final payloads are installed through smart contracts that hackers place on both the Ethereum and BNB Smart Chain blockchains, which permit uploads from anyone.
One of the teams Google detected, a North Korean-supported group known as UNC5342, employs earlier-stage malware identified as JadeSnow to fetch later-stage malware from both the BNB and Ethereum blockchains. The researchers at Google noted:
It is atypical to observe a threat actor utilizing multiple blockchains for EtherHiding operations; this could suggest operational compartmentalization among North Korean cyber operator teams. Moreover, campaigns frequently exploit EtherHiding’s adaptable nature to modify the infection chain and alter payload delivery sites. In a single transaction, the JADESNOW downloader can transition from retrieving a payload on Ethereum to obtaining it on the BNB Smart Chain. This transition complicates analysis and taps into the lower transaction fees available with alternative networks.
The researchers also observed another faction, the financially motivated UNC5142, also using EtherHiding.
North Korea’s hacking capabilities were once viewed as subpar. However, over the last decade, the nation has conducted a series of prominent attack operations that showcase increasing skill, focus, and resources. A fortnight ago, blockchain analysis firm Elliptic reported that the country has pilfered cryptocurrency worth more than $2 billion this year alone.