From the Department of Bizarre Anomalies: Microsoft had been masking an unexplained issue on its network that forwarded traffic intended for example.com—a domain reserved for testing purposes—to a Japanese maker of electronics cables.
Under the RFC2606—a formal specification from the Internet Engineering Task Force—example.com is reserved and cannot be claimed by any party. Instead it resolves to IP addresses managed by the Internet Assigned Names Authority. The designation exists to stop third parties from being flooded with traffic when developers, penetration testers, and others need a placeholder domain for testing or technical discussion. Rather than using an Internet-routable name, they should use example.com or one of the other reserved names, example.net and example.org.
Misconfiguration cleared — but is it resolved?
cURL output shows that systems inside Azure and other Microsoft networks were sending some traffic to subdomains of sei.co.jp, a domain owned by Sumitomo Electric. Most of the returned content looked normal; the exception was the JSON response. Here’s the JSON output from Friday:
{"email":"[email protected]","services":[],"protocols":[{"protocol":"imap","hostname":"imapgms.jnet.sei.co.jp","port":993,"encryption":"ssl","username":"[email protected]","validated":false},{"protocol":"smtp","hostname":"smtpgms.jnet.sei.co.jp","port":465,"encryption":"ssl","username":"[email protected]","validated":false}]}
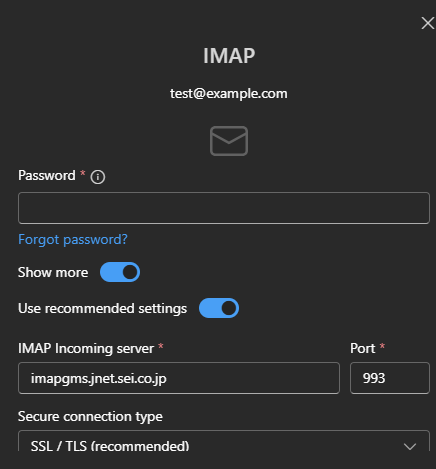
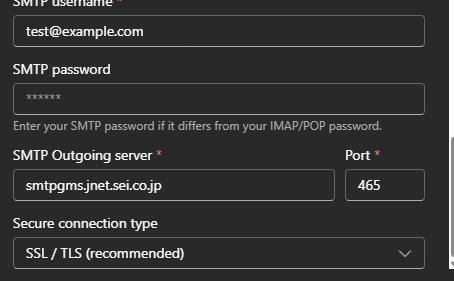
Similarly, when adding a new account for [email protected] in Outlook, the results appeared like this:
In each instance, the outputs indicate Microsoft was directing mail traffic to two sei.co.jp hosts: imapgms.jnet.sei.co.jp and smtpgms.jnet.sei.co.jp. This behavior originated from Microsoft’s autodiscover service.
“I won’t claim to be an expert in Microsoft’s internals, but this looks like a straightforward misconfiguration,” Michael Taggart, a senior cybersecurity researcher at UCLA Health, said. “As a result, anyone setting up an Outlook account for example.com could inadvertently transmit test credentials to those sei.co.jp subdomains.”
Asked early Friday afternoon why Microsoft was doing this, a representative had no explanation and asked for more time. By Monday morning the improper routing had stopped, but the representative still offered no explanation.